Understanding Confidential Computing (feat. Ilja Aizenberg, M Ventures)
The most important bit of hardware, you've never heard of.
I’m Lawrence Lundy-Bryan. I do research for Lunar Ventures, a deep tech venture fund. We invest €500k-€1m at pre-seed & seed to turn science fiction into science reality. Get in touch at lawrence@lunar.vc. I curate State of the Future, a deep tech tracker and every week; I explore interesting stuff in deep tech. It’s for people who don’t take themselves too seriously. Subscribe now before it’s too late.
This week is our first #collab. The best collab since Kano brought Wiley and Giggs together on 3 Wheel-ups. Some MCs come with the wickedest talk.
Lunar x M Ventures. Lawrence x Ijla. Ilja is a Principal at M Ventures, the corporate VC of Merka KGaA. He is among the smartest thinkers on privacy-enhancing technologies in data infrastructure today. Ilja and I have been batting around the future of privacy-enhancing technologies for the past few years, and we both agree that trusted execution environments (TEEs) are a significant part of the future cloud aka confidential computing (CC).
You can read more about how TEEs fit into our “collaborative computing” thesis
Also, if you like your explanations from first principles with code examples, I recommend the below over atWhy Nowby Alex Mackenzie.
3️⃣ things
Here’s 3 things you should read. Just 3 things. If I don’t see some click-through rates, what are we all doing out here? Click the links.
A desalination system could produce freshwater that is cheaper than tap water.
Can robotics take off like GenAI? Moravec's paradox vs. scaling laws Interconnects
Deep Thought, Deep Learning and the World's Total Computing Resources The Chip Letter
🙏 Thanks for reading, Lawrence (x Ilja)
🔒TLDR: Trusted Execution Environments (TEEs)
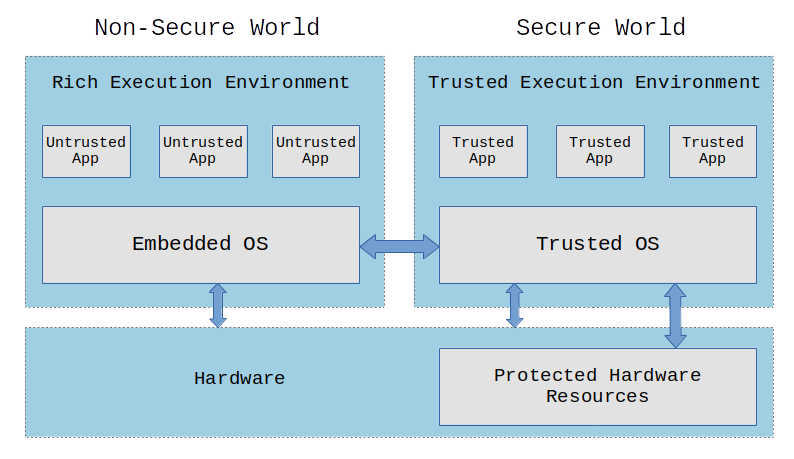
📋 Summary: Trusted Execution Environments (TEEs) are secure areas inside a main processor. They operate as a "secure enclave" to protect critical functions from the rest of the system.
🚦Viability [5/5]: After 13 years of commercialisation with 1 billion units sold, TEEs are mature and cheap enough for continued growth across mobile applications and begin penetrating data centre applications via confidential computing.
🥇 Novelty [4/5]: The only hardware-based solution to protect sensitive data and code, TEEs are cheaper and less computationally expensive than software-based privacy-enhancing technologies like FHE, MPC or ZKP. They are, however, inherently less flexible and scalable.
🚘 Drivers [4/5]: Mobile payments, digital rights management (DRM) and confidential computing are the primary adoption drivers with 20-30%+ annual growth.
✋ Diffusion [4/5]: Offered by every significant hardware and cloud vendor, the main difficulty remains market education and cumbersome implementation of confidential computing, but these restraints are limited and off-the-shelf solutions are coming to the market
📈 Impact [4/5]: There is a high probability of high impact because the core proposition of limiting data breaches is compelling. But more importantly, part of a broader shift to a confidential, collaborative computing environment in which orders of magnitude, more data is available for processing and ML models.
🕰️ Timing [2020-2025]: Now. Market worth between $5-10 billion, growing somewhere in the order of a massive 50% annually.
💯 Rating [Underrated]: Correctly rated by industry, but likely mainstream, including users and investors, yet to understand pervasiveness today and massive market growth rates.
🔮 2030 Prediction: By 2030, 85% of all new SoCs shipped by leading vendors will contain integrated TEE enclaves.
💡 Opportunities:
Migration of sensitive on-prem workloads into the cloud.
Collaborative computing applications that combine TEEs with other PETs for revenue-generating, not security/cost-saving activities.
Vertical-specific developer tooling on cloud VMs to abstract away TEEs and make deployment more accessible and faster.
🔒Trusted Execution Environments (TEEs) Overview
📋 Summary
Trusted Execution Environments (TEEs) are secure areas inside a main processor. TEEs provide hardware-level isolation and security for sensitive code, data, and applications. They operate as a "secure enclave" to protect critical functions from the rest of the system. TEEs allow devices to store and process confidential data such as passwords, biometrics, encryption keys, and financial information in an isolated environment safe from malware and hackers. Initially defined by the Open Mobile Terminal Platform (OMTP) in their "Advanced Trusted Environment: OMTP TR1" standard, TEEs were first commercialised around 2010 in SIM cards by Nokia and later other mobile manufacturers. Today, TEEs have applications across many verticals, including payments, content protection, authentication, automotive, and IoT. They enable services like mobile payments, DRM-protected video streaming, biometric authentication for mobile banking, and firewalls for connected cars. More recently, TEEs are offered via virtual machines for confidential computing applications to process sensitive code and data in the cloud securely.
🚦Viability [5/5]
The first generation TEEs launched in 2010, and the past 13 years have steadily progressed. Today, all major processor vendors now support TEEs, including ARM TrustZone, Qualcomm Secure Execution Environment (QSEE), Samsung Knox, Huawei iTrustee, AMD Secure Processor, and Intel Software Guard Extensions (SGX). Apple first shipped their Secure Enclave in 2013 and now includes them in its entire product range, from iPhones, iPads, Apple Watches, Apple TVs, and Macs. Collectively, there are likely a few billion TEEs out in the wild. Regarding R&D, the most important innovation has been to extend TEEs to the cloud. This extension now goes by “confidential computing”, which uses TEEs to enable secure data processing while in use. Much of the R&D today is in integrating TEEs with the broader confidential computing stack and improving security. There were side-channel attacks demonstrated against TEEs, mainly during the 1st generation of Intel SGX, that indicate they may not be completely secure in all scenarios, such as cache side-channel attacks, branch shadowing and power side-channel attacks. Most of these concerns have been resolved with the 2nd generation of TEEs for confidential computing, such as in Intel Trust Domain Extensions (TDX).
🥇 Novelty [4/5]
TEEs are a tool to secure sensitive code and data. TEEs represent a novel approach to security by building it directly into the underlying hardware rather than relying strictly on software defences. Alternatives for securing sensitive data include traditional software methods like firewalls and access controls, but these solutions are materially weaker in security terms. More robust solutions include advanced encryption techniques like zero-knowledge proofs (ZKP), multi-party computation (MPC) and fully homomorphic encryption (FHE).
TEEs provide a potent combination of security, performance and maturity, making them a preferable solution for many use cases today. The on-chip environment enables secure computation on live data with minimal overhead, mature software stacks for deployment, and protection against software and physical attacks. Compared to ZKP, MPC or FHE, TEEs have orders of magnitude lower computation and communication costs, offering negligible latency in most use cases. They also benefit from widespread production deployment, especially on mobile devices. However, TEEs, significantly earlier implementations such as Intel SGX, have some limitations in their threat model. They rely on the integrity of the hardware and focus on protecting it from external software attacks. Side-channel attacks that monitor cache, branch activity or power usage could leak secrets from a TEE. Alternatives based on cryptographic methods like MPC, ZKP, and HE inherently protects against some side-channel risks by avoiding direct computation of raw secrets. While they have higher overheads, they provide security even from a malicious execution environment. So, for some applications dealing with adversary control of the hardware or physical access, alternatives to TEEs may be more suitable despite higher costs.
However, rather than viewing TEEs and software-only PETs as competing, the most secure solution will likely use TEEs AND. Not TEEs OR. Systems can mitigate software and physical side-channel risks by combining TEEs with cryptographic methods like masked computation, secret sharing, and other defences integrated at the algorithmic level. This blended approach provides strong hardware isolation and mathematical protection within the TEE.
For confidential computing use cases, modern cloud stack architectures offered through Azure, AWS Nitro, and GCP, deployed on Intel TDX or AMD-SEV, typically virtualize the TEE concept through sealed Virtual Machines rather than using the limited resources of dedicated on-chip memory in its original form. Nevertheless, TEEs are the foundation for the hardware-based root-of-trust attestation mechanism, which provides users of confidential computing with a cryptographic proof of compute infrastructure, and application code and data integrity.
🚘 Drivers [4/5]
TEE adoption is driven by mobile payments, DRM, and, most recently, confidential computing for lift & shift workload migration of legacy applications to the cloud. With about 50% of workloads still residing on-premises due to security concerns in public clouds, confidential computing offers a strong value proposition to finally use cost-efficient and elastic cloud architecture for these sensitive workloads. Further, the massive expansion of mobile payments and financial transactions is a significant driver propelling TEEs. Apple Pay, Google Pay, and Venmo enable tap-to-pay and peer-to-peer payments from mobile devices. TEEs provide secure enclaves to store payment tokens and biometric templates for user authentication. Similarly, the boom in streaming high-value copyrighted content like movies and sports depends on robust DRM and antipiracy mechanisms. Services like Netflix, Hulu, and Spotify use TEEs to secure media delivery and playback on user devices. They allow smooth streaming while preventing content leaks that would undermine the industry's economics. Mobile media consumption is projected to grow 33% annually, fueling TEE uptake.
TEEs are the solution for cloud vendors who, in 2019, formed the confidential computing consortium (CCC) to advance cloud adoption. Formed in 2019 by Alibaba, Arm, Baidu, Google Cloud, IBM, Intel, Microsoft, Red Hat, Swisscom, and Tencent, the CCC has sought to advance confidential computing adoption across cloud, enterprise, and industry verticals through open-source collaboration. It’s not quite the same as TEEs, but there are forecasts of a 50% CAGR growing into a $150-200 billion market by 2030. However, I wouldn’t trust those forecasts when it is in the interests of a large, well-financed lobby group to talk up a market.
✋ Diffusion [4/5]
While the appetite for TEE security is expanding rapidly, there are still hurdles to seamless mainstream adoption. One constraint is the tight confines and heat sensitivity of mobile chip architectures - it is challenging to integrate TEE capabilities within small form factors like smartphones and wearables. This requires efficient TEE design and coordination among IP vendors to minimise footprint and power draw. Additionally, adding TEE security into legacy software systems and applications is complex. This is particularly impeding deployment of confidential computing use cases where large applications, with memory and cross-cloud communication capabilities, are required, such as LLM-based business models. Using confidential computing usually requires entirely new approaches to partitioning sensitive data and flows away from traditional operating systems and hypervisors. TEEs shine in new ground-up application development, but integrating them into existing frameworks remains difficult. Rewriting millions of lines of code is arduous, but a few startups successfully address these issues, paving the way towards confidential computing as the next-gen cloud standard. Attack vectors like side-channel attacks against TEEs require vigilance, although these risks are mitigated for cloud solutions. (Edit: emailers telling me that the risks cannot be mitigated). Though hardware security provides fundamental advantages, no solution is perfect, and TEE protocols need to evolve to stay ahead of new hacking techniques.
First principles make the case for software-based cryptography like FHE or ZKP winning in the long run (7-10 years). TEEs need hardware and cannot be updated quickly or cheaply. A security risk cannot be patched and fixed without new hardware. However, in 2023, software-based cryptography is too expensive, both computationally and in terms of expertise. So, as TEEs go from 1+ billion devices to 5+ billion devices over the next 3-5 years, the security landscape will have improved, from very bad to decent. The leap from decent to excellent that we can achieve with software-based cryptography will take longer for mainstream adoption as the pain will be less intense for buyers.
📈 Impact [4/5]
It’s not a bold shout to say TEEs will have a high impact, with others already predicting 50-100% growth rates in the next few years and the value proposition compelling and clear. Mobile payments are growing by 20-30% annually; mobile content consumption is increasing. And that’s before cloud adoption, which could be even faster. The difficulty in predicting long-term TEE impact is that, from first principles, software-only solutions should be more secure and cheaper. However, the need to secure and shift sensitive code and data to the cloud is high today, and TEEs are better than we have now and cheap solutions. However, the real high impact comes from the new functionality and behaviours enabled by TEEs, not the efficiency and security benefits for existing applications. TEEs are part of the broader shift to a “collaborative computing” environment in which users feel more comfortable sharing sensitive data outside of the corporate borders, and owners of ML models can make these models accessible in the cloud while protecting their IP. This shift will take time and benefit further from adopting cryptographic techniques like MPC and FHE. Still, it will ultimately lead to an order of magnitude more data available for collaboration and powerful AI applications.
We suspect TEE adoption will be rapid over the next few years and in 3-5 years. When software-only solutions are cost-competitive, the sunk costs of TEEs and the relative benefits of upgrading will make TEEs dominant long into the 2030s. In the 2035+ timeline, we can’t see a scenario where software solutions don’t ultimately replace hardware, so we can’t score TEEs 5 or 5+.
🕰️ Timing [2020-2025]
The confidential computing market was $5 billion in 2023. This aligns with bottom-up estimates for the use case enterprise workload migration alone. However, there isn’t credible data on TEEs, which is frustrating. But for this assessment, the only thing that matters is the growth rate. As noted, I don’t trust the current market forecasts, but still, they do average out at 25-50% annual growth rates, rather than 5-10 or 10-20%. And these numbers are likely just counting data centre demand. If you add in mobile and embedded demand, the demand is enormous. These growth rates, from not a tiny base, make TEEs investable today. Better yesterday. For context, TSMC, AMD and Nvidia forecast 50% annual growth for the next 3 years, then roughly 25% for the next two years for AI accelerators in the datacenter. And did we mention, that NVIDIA’s H100 will come with TEEs? Reading the numbers here, TEEs will grow faster than AI chips for LLMs? Well, @Elad and I think Nvidia are underestimating demand, maybe even by 2x. But that’s a story for another day. Still, TEEs may very well be one of the fastest-growing technologies in the State of the Future.
💯 Rating [Underrated]
Despite billions of people using FaceID, few realise how prevalent TEEs have become. Within the industry, people certainly do not underrate the opportunity. That’s why the CCC launched with many heavy hitters, including Alibaba, ARM, Baidu, Google, Intel, Microsoft, and Tencent. It was underrated in 2018 but probably correctly rated in 2023.
But even after writing about TEEs very positively in the collaborative computing paper in 2021, we are surprised at a 50% projected growth rate. So, on balance, it is underrated.
❓Open Questions
Why isn’t Amazon in the CCC? They use their Nitro enclaves already; is it a simple case of them choosing proprietary over open? Seems weird.
Alibaba, Baidu and Tencent are all in the CCC, the aim of which is to encourage enterprises to store their sensitive data in the cloud. Geopolitics much?
It is still painful to deploy confidential computing applications in production, especially when it comes to memory and cross-cloud capabilities. Will a third generation of cloud technology make it easier for enterprise users?
TEEs are cheaper than software-only cryptography, but there will be niches for which heavily optimized cryptography can be competitive. FHE like Zama for ML inference? Private information retrieval protocols for database querying? How many niches are there, and how large can they be? Is a useful model TEEs for general compute (CPU) + other PETs for specific workloads? (ASIC)
💡 Opportunities
Collaborative computing applications combine TEEs with PETs like MPC, ZKP or FHE for “full-stack” security.
Vertical-specific middleware on top of Azure Confidential Computing, AWS Nitro Enclaves, GCP Confidential VMs, like Fortanix Confidential Cloud, and Anjuna Security, making it easier for developers to build applications without having to manage TEEs
Collaborative zero-trust platforms, especially for regulated industries like government, healthcare and financial services.
🔮 2030 Prediction
By 2030, 85% of all new SoCs shipped by leading vendors will contain integrated TEE enclaves. Every code and data on cloud VMs will be run via confidential computing by default with an opt-out possibility.
📺 Startups to Watch
Fortanix (https://www.fortanix.com/) - Provides confidential computing solutions leveraging Intel SGX and AMD SEV for key management use cases. Offers a runtime encryption platform.
Anjuna Security (https://www.anjuna.io/) - Enables easy deployment of confidential computing across any cloud environment at an enterprise scale.
Oasis Labs (https://oasislabs.com/) - Combining Intel SGX with blockchain to offer a confidential computing platform for secure data storage and computation.
Scone (https://sconedocs.github.io) - Aiming to make confidential computing and TEEs like SGX easily accessible to developers through open-source tools.
Edgeless Systems (https://www.edgeless.systems) - Provides open-source solutions for confidential computing.
Cape Privacy (https://capeprivacy.com) Focuses on LLM privacy and uses a couple of tools, including AWS Nitro.
Post publishing additions:
CanaryBit. (https://www.canarybit.eu) Confidential data sharing and processing between Businesses and Public Authorities.
Enclaive (https://enclaive.io). The enclaive multi-cloud platform shields data and application code within a fully encrypted and confidential and auditable black-box, known as an “enclave”.
Encloud (https://encloud.tech). Secure, private and scalable data platform for developing and deploying your AI. Built on top of any cloud or on-prem hardware
Flashbots (https://www.flashbots.net). Flashbots is a research and development organization formed to mitigate the negative externalities posed by Maximal Extractable Value (MEV) to stateful blockchains, starting with Ethereum.
iExec (https://iex.ec). iExec is a blockchain company that allows anyone to monetize or rent computing power, datasets, and applications.
And it’s bye from me. And bye from him. Ilja is a Principal at M Ventures, the corporate venture capital arm of Merck KGaA, Darmstadt, Germany.





Nice article, just a small nit: guess the "cloud computing consortium" is meant to read "confidential computing consortium"